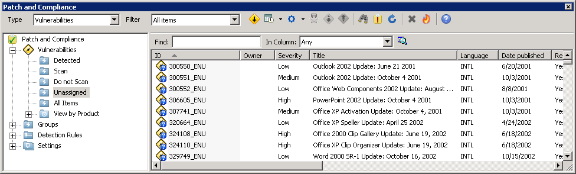
Adventures in Automation: Introduction to Vulns, Common Vulnerabilities and Exposures, the CVE List, and the National Vulnerability Database

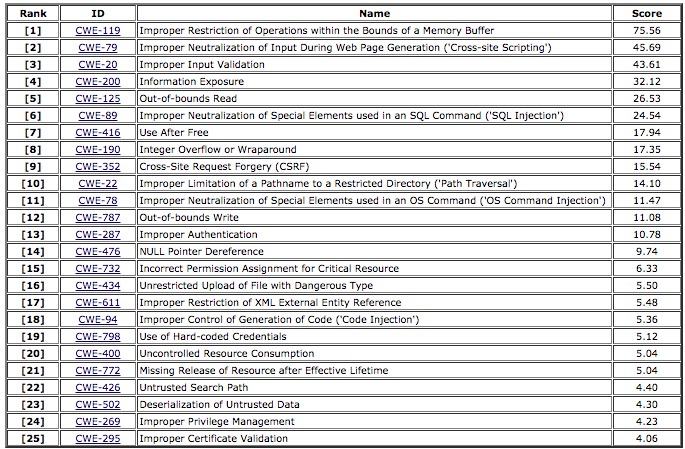
IPA Information-technology Promotion Agency, Japan : IPA/ISEC:Vulnerabilities:CVE (Common Vulnerabilities and Exposures) Overview
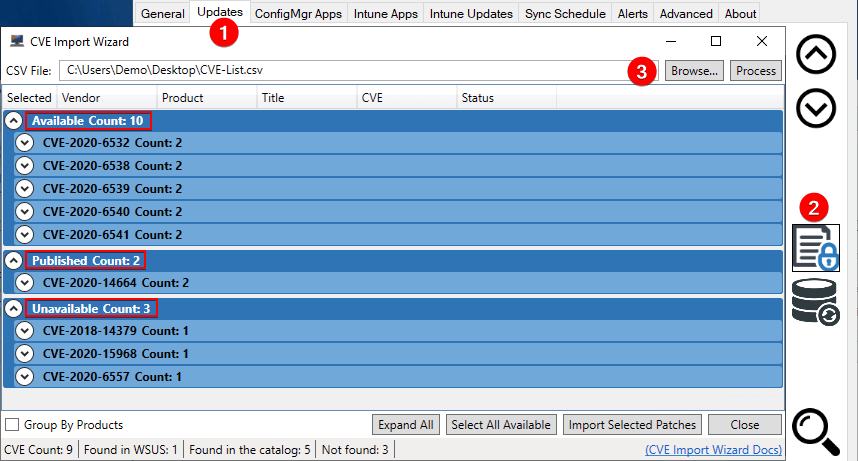
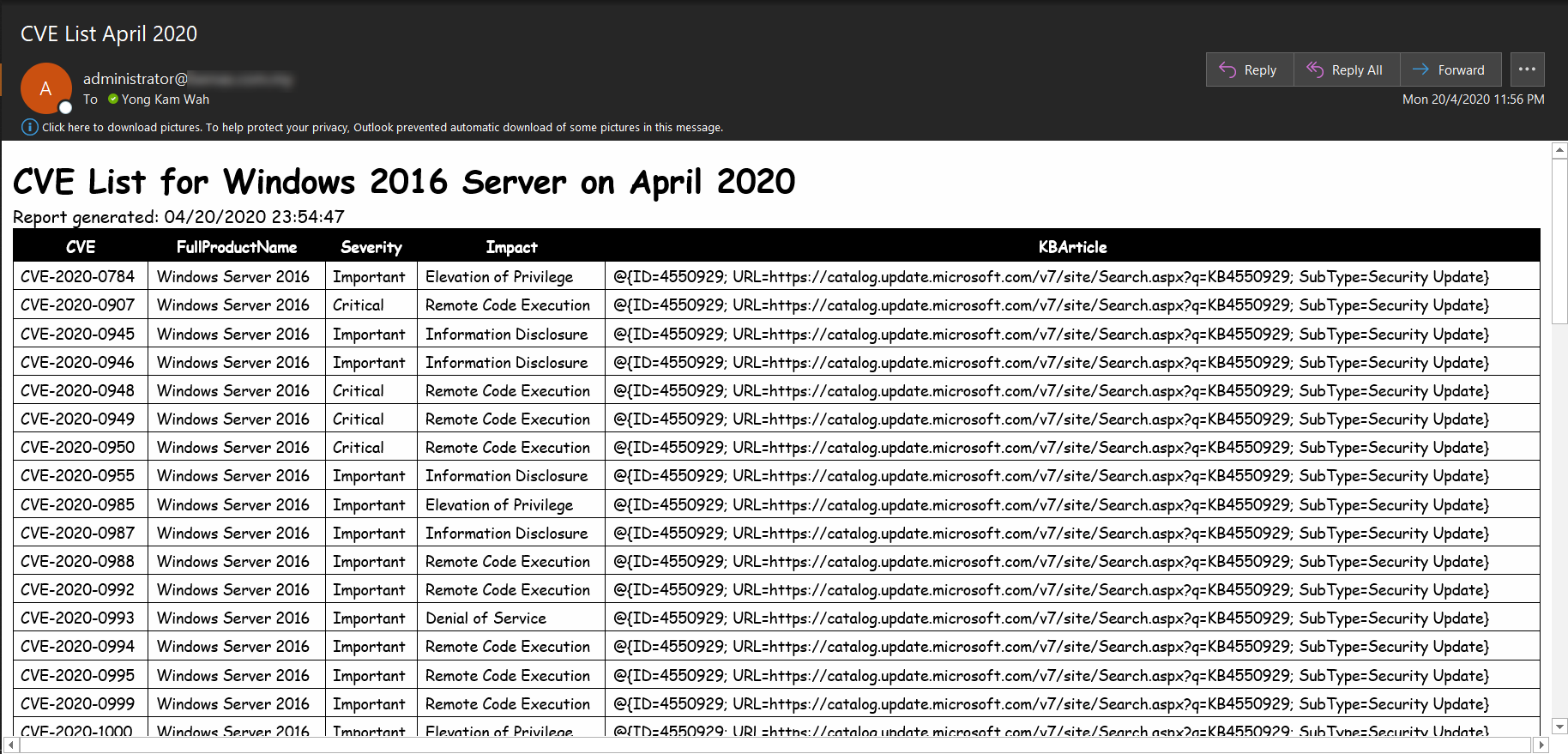
cve_manager_VS - A Collection Of Python Apps And Shell Scripts To Email An Xlsx Spreadsheet Of New Vulnerabilities In The NIST CVE Database And Their Associated Products On A Daily Schedule

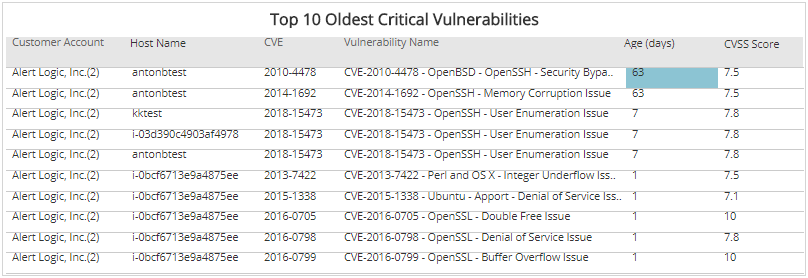
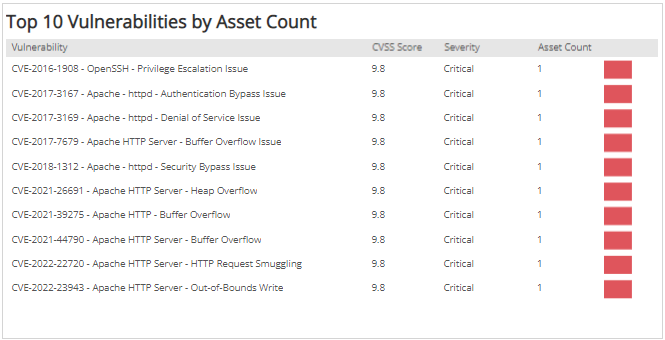
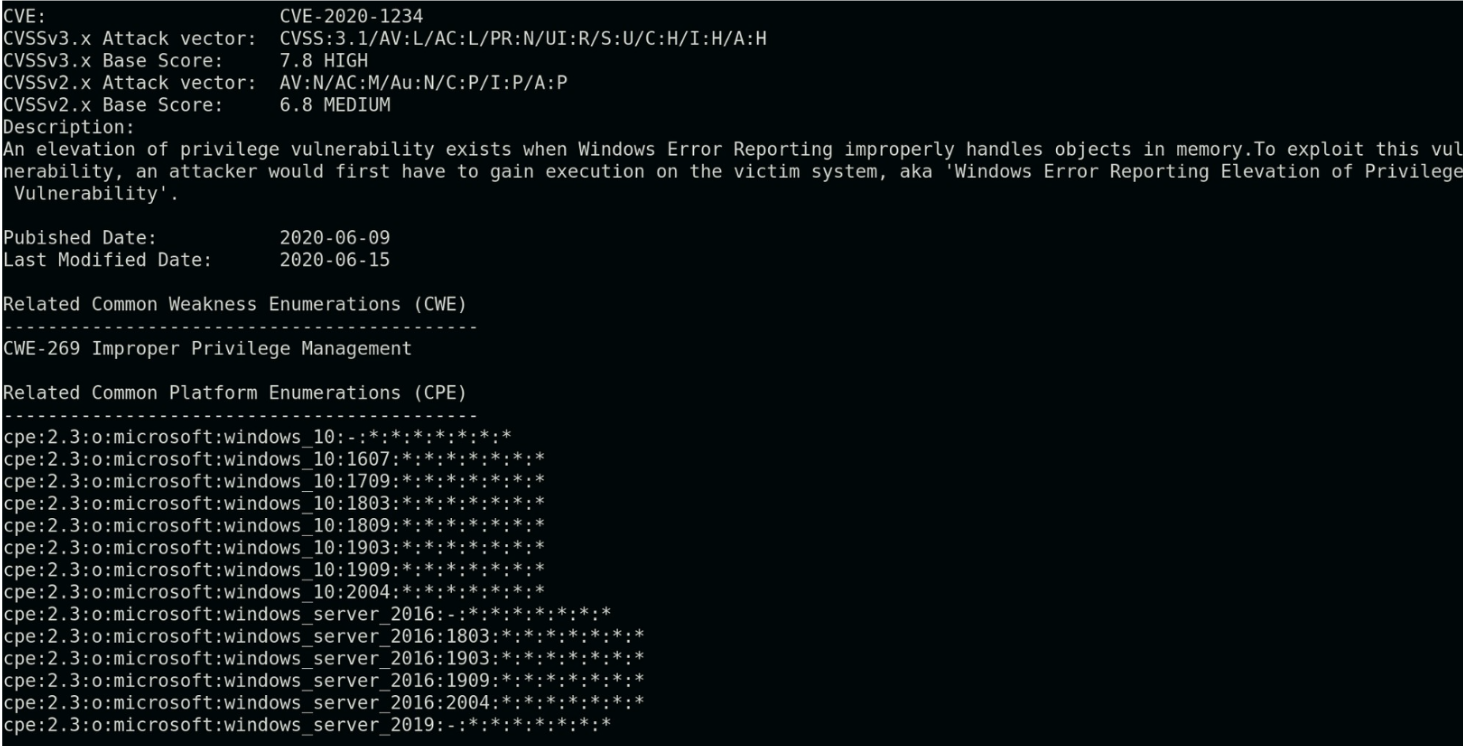
Example CVE from cve.mitre.org Each CVE includes metadata such as a... | Download Scientific Diagram